CES Communications takes GDPR compliance and privacy matters seriously. Below you will find our general sample guidelines; for a more in-depth and personalized statement, please contact us directly.
Please note that the information below is intended to be a generalized sample and is not legally binding. For specifics as they relate to your project, please contact us directly.
Compliance Statement
General Data Protection Regulation – Goes Live May 25 2018
As the data protection laws are changing in the European Union, so too will our compliance requirements. Since CES Communications and all entities belonging to the CES Communications group of companies are entirely housed within the European Union, General Data Protection Regulation or “GDPR” compliance will be regarded with the utmost importance. The GDPR brings about a higher level of security and data handling standards and CES Communications have focused on meeting or exceeding the required standard in every aspect of their business.
As a data processor, CES Communications’s compliance also extends beyond the organization to the data controllers and sub-processors with whom we work. Our standard of excellence in data management is shared with our customers (data controllers) and our providers (data sub processors) ensuring that data subject’s best interests and security are at the forefront of every transaction in which we participate.
We also extend these same courtesies to our clients and contractors, ensuring that we only gather and process what is absolutely necessary and where Personally Identifiable Information (PII) is present, that information securely encrypted from the time it leaves our client, through all processes performed, right up until the time we dispose of the PII.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Methodology
Excellent processes yield exceptional results.
At CES Communications, our standard of excellence applies directly to our commitment to data security, data subject privacy and total transparency. In order to achieve the requisite demands as placed on the firm by the GDPR, we conducted an internal audit on our data, our processes and the providers with whom we work. The end result of this audit yielded the following results with respect to process improvements in personal data processes:
Audit Results
We looked at the way we receive data, store data, process data, report on data and dispose of data and identified the following:
- The amount of data which we require from the Controller will be limited to just those fields that allow us to perform our applications efficiently.
- The manner in which we process data will be prescribed, approved and legitimately in the best interest of our clients balanced to the rights of the data subjects.
We will not retain PII for longer than 120 days, in most cases only 14 or 90 days. We will however retain non-PII details that allow us to understand if we have attempted to contact data subject in the past to prevent unwanted solicitation. In the event that we see the same unique identifier from the same controller, only then will the non-PII history be reused.
Data processed will include validation to ensure accuracy and correctness.
We have implemented security protocols that are intended to follow more than just the letter of the GDPR but also the spirit of constant awareness that the data of the subject should be protected and “forgettable” at any point in our processes or at their request.
An important part of respecting the letter and the spirit of the GDPR is the commitment to continually auditing our processes to identify if we can achieve more, with less (data) and or if we change a process, does the benefit of the change balance both the rights of data subjects and the benefits to the clients.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Data Security
CES Communications has structured their Information Security Team to leverage the highly qualified resources and specializations available.
The hosting operations of the CES Communications systems are managed by Image Arts GmbH. The hosting operations CTO is the only person who has complete access to the systems/data. As a neutral third party and data security specialist this was deemed to be suitable fit to satisfy the restrictions surrounding data access and GDPR compliance.
CES Communications has designated and trained team members that handle the provisioning/disabling of new agents, as well as handling routine network/server maintenance (i.e. back-ups, firewall configurations, etc.)
All members of the team have received GDPR compliance training and are aware of the rights of the data subjects.
The servers used by CES Communications are located in a Tier3+ datacentre in the west of Germany (Düsseldorf). The Environment (physical access, housing, cooling, backbone connect, energy) is operated by the Myloc managed IT AG.
CES Communications retains two application architects who help create the strategic technical direction for the CES Communications software and ensure that it meets the requirements of our clients and fulfils our obligations in the new GDPR environment.
- Right to Access
- Right to be Forgotten
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Information Security as a Standard Including Restricted Access, Encryption and Monitoring
Physical server side access resides outside the reach of CES Communications developers, architects and management, massively reducing the potential for a physical data breach to occur. When anyone requests access to servers, the request is first considered by management and then, if approved, is closely monitored. Access can only take place through VPN and with a pre-approved IP address.
- Even if the requested access involves access to the database, all Personally Identifiable Information (PII) fields are encrypted using a 256 bit AES with the encryption keys stored remotely.
- Each week all access is monitored and reported on, with a review process taking place across a team of people.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Processing Provisions
As a data processor we take what we do seriously and through collaboration with our legal representatives, have updated the ways in which we process the data that is passed from the data controller, to our system. The contracts we have in place with our customers remain in effect but the requirements of GDPR have brought about changes to a number of the provisions with respect to the processing of data subjects, their rights and the storage and disposal of such information. Those changes can be found in our updated data processing agreement (DPA) which is a requirement under the GDPR and allows us and our clients to fully understand the nature and expectations surrounding data transfer, data security, data storage, data processing, and disposal of PII.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Data Processing Agreement
You must be a client to obtain a copy of our data processing agreement. If you wish to become a client, please contact us.
Request to Access
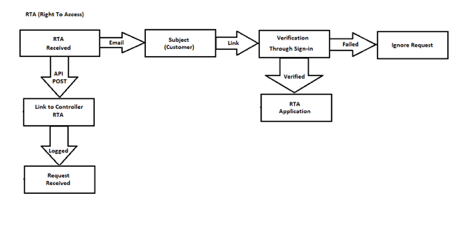
Request to be Forgotten
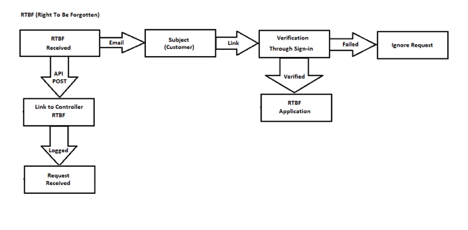
Acknowledging the Data Subject’s Request to Access (or Be Forgotten)
CES Communications will track all applications that are received with respect to data subject’s requesting access to their personal information. In addition, these access requests will be logged and monitored to identify if there are process improvements that can be made to reduce the impact and timeliness of such requests with all PII being removed from this logging and monitoring.
Failures to respond adequately to data subject requests will be investigated on a case by case basis and reviewed. Accusations of incomplete requests will trigger an internal audit on the process and the subject, if requested, will receive a full report on the audit’s findings with a proposed resolution to the accusation provided.
Escalations will be identified and if required a 3rd party, such as an auditor or legal representative may be informed to help provide the necessary guidance to protect all involved parties best interests.
Generate a Formal Request via Email or SMS for the Subject to Access
Formal requests to access information will primarily be generated via email, with the understanding that CES Communications and its associates cannot access the subject’s email (encrypted), it may result in an incomplete transaction request. In those cases, the data subject may request to access their information through a link sent via SMS, again which can be sent to the number that was provided to the controller. If neither of those work, the request to access will be escalated to the controller for further assistance.
Access Requests – Subject to Validation
CES Communications will provide a direct link via email or SMS, to the data subject requesting access to their information. At that point the data subject will be required to access the account by way of password, which would have been supplied by the data subject at the time of account registration. If they are unable to provide that password, the data subject will also have the opportunity to utilize the support personnel of the data controller to gain access to their requested information.
In the event that a further investigation is required and CES Communications is required to apply additional resources to the investigation, a fee for services may be applied, if in any event it is apparent that the request is outside what would be reasonably expected through the normal course of the data subject’s request to access.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Requests Specific to CES Communications Processing
CES Communications agrees to Process the Personal Data held by the Data Controller only on the instructions of the Data Controller and on the basis of the following grounds:
- The Data Subject has given consent to the Processing of his/her Personal Data to the Data Controller for a specific purposes;
- Processing is necessary for the purposes of the legitimate interests pursued by the Data Controller and/or the Data Processor and/or any third party
During the course of their normal activity, CES Communications will ONLY act on behalf of the data controller and with the balance of data subject privacy, having been considered.
If during the tenure of a communication, a client request is specific to the marketing communication that is taking place, CES Communications is prepared to provide:
- A logical and just reason for the processing of the subject’s data
- All fields of personally identifiable information that has been extended to CES Communications
- The partners with whom the data has been processed through during the course of the marketing activities
- Proof of compliance on the parts of each of the sub-processors
- The manner in which the data subject’s data has been secured, stored and processed
Open communications expressly concerned with a resolution to the inquiry and satisfactory outcome for all parties including but not limited to:
- The data subject
- The data controller
- CES Communications
- Any other party whom might be lawfully involved in the request
- The data subject’s right to the following:
- Be forgotten
- Access
- Understanding
- Origin of the data
Document and Retain Subject Access Requests
Subject access requests will be anonymized, retained and logged for future reference and process improvement. Monthly reports will be audited internally and systematically monitored to maintain the highest standards.
Open access requests will remain open until such time as they are resolved or if 120 days elapses since contact is made from the data subject.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Data Protection
Introduction
CES Communications, through their normal course of operation, requires the gathering and processing of personal information from the following groups:
- Contractors (callers, translators, auditors, developers, operations specialists etc.)
- Suppliers (network service providers, industry professionals, designers, etc.)
- Clients (data controllers and in some cases, data processors who have requested the controller to contract CES Communications )
All data pertaining to these parties will be treated with stringent policy and used only in the due course of conducting business. At any time, at the request of the data subject in any of these groups, CES Communications will extend the full and very same rights as apply to all data subjects.
In an effort to afford the full rights afforded to data subjects under the new GDPR compliance, CES Communications has made it a policy to inform all individuals that they must adhere to the strict data privacy regulations and first and foremost respect the data of those with whom they operate alongside in the organization. Ongoing efforts to further the knowledge and respect for the internal data will continuously be developed and documented. For more information on how data in three (3) categories above will be treated, please fill out the contact form below and we will respond to your query within two (2) business days.
CES Communications has defined the following policy with respect to the three underlying principles that must be trained and adhered by those parties working with CES Communications:
- Data Security
- Data Usage
- Data Retention
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Data Security
CES Communications and their associates have been briefed both verbally and through documentation, with respect to the sensitive nature of some of the data with which they may come in contact in their natural daily routines within the organization. The corporate stance on this internally generated data is that it remains that of a “natural person” and is therefore entitled to the highest degree of privacy that can be afforded which includes but is not limited to electronic copies, hard copies (paper) and even in the course of speech, the right to privacy is to be regarded and respected with no unauthorized access or disclosure of any sort being tolerated. While this entitlement to personal data security is generally assumed, CES Communications ensures their people and those with whom they work closely are briefed via a notification explaining the following as identified in Article 4, under the GDPR definitions:
personal data’ means any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person;
Source: https://gdpr-info.eu/art-4-gdpr/
By creating an understanding within the organization that personal data is not to be disclosed except where deemed necessary as a job “process” and or a legal requirement, allows not only for the feeling of security but also for the knowledge of respect that accompanies the responsibility that has bestowed upon those associates.
If in the event, as required from time to time, a hard copy is created, the hard copy is to remain whole only for the period necessary to complete the intended “process” and it is the assigned responsibility of the printer to destroy that hard copy as soon as possible. During the course of their existence, paper copies containing any PII are to be:
- Locked filing cabinet or other “lock and key” office storage space
- Remain in a secure facility
- Accessible only by those who have been authorized to do so
- Stored only for the time as prescribed by the creator of such hard copies (in the event the creator leaves, the replacement party shall assume this duty of security)
- Destroyed when the intended purpose has been fulfilled
With the more easily transferrable copies, CES Communications takes extra care and attention by following these rules:
- Stored securely in a central place on corporate servers that requires VPN access
- PII will be encrypted while in a state of storage
- User access of such data will be logged and monitored
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
CES Communications Internal Communications Policy
With the GDPR regulation coming into place, the people working within the CES Communications and the associates therein have been trained to understand that communication channels that are not controlled on the corporate network are not always secure. Associates are not to send personally identifiable information via channels that are not encrypted or controlled internally. Associates are encouraged to bring about ideas that can assist the company enhance their knowledge and respect for ways in which we can process and protect the personal data of those parties with whom we work.
By recognizing that centrally stored and accessed data is more secure, CES Communications has encouraged their associates to abide by this as it prevents the potential breach associated with misplaced or stolen equipment. In the event that equipment is “lost”, the personal data that was accessible via electronic copy will have been secured via password or encryption but the Data Breach Policy Document (DBPD) procedure will be followed.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
CES Communications and their Network of Sub-Processors
As a provider of multi-channel marketing services, CES Communications and its associates as required to work with a number of Sub-Processors. Each of those sub-processors has been vetted as being GDPR compliant and in the event of Brach notification from one those suppliers, CES Communications will again follow their DBPD, notifying in the correct order and timeliness, the affected parties. All Sub Processors are required to have provided adequate documentation with regard to the GDPR compliance, a legally binding contract or agreed to terms of service, sufficient security measures and policy surrounding potential data incidents.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Data Usage
Under the GDPR, data processors (like CES Communications ) that are contracted for the usage of personal data as held in trust by a data controller must follow at least one of the six (6) lawful bases for processing of data which then must be balanced against the right to privacy on the part of the data subject.
In order to create the required balance CES Communications has reviewed our purposes for processing activities and taken significant steps to reduce the amount of data requested from the controller. The ways in which we process the data have also been minimalized and at every possible interaction, the data subject is granted to right to cease further communication through any one, a number of or all channels and that too will extend to the controller as well. Further to the decision to continue processing data, we find the following lawful bases are the ones most applicable for the communications that are authorized through our channels:
- Consent: the individual has given clear consent for you to process their personal data for a specific purpose.
- Contract: the processing is necessary for a contract you have with the individual, or because they have asked you to take specific steps before entering into a contract.
- Legal obligation: the processing is necessary for you to comply with the law (not including contractual obligations).
- Legitimate interests: the processing is necessary for your legitimate interests or the legitimate interests of a third party unless there is a good reason to protect the individual’s personal data which overrides those legitimate interests.
Source: https://ico.org.uk/for-organisations/guide-to-the-general-data-protection-regulation-gdpr/lawful-basis-for-processing/
In the course of our regulation obligations to the data controllers, Consent and Legitimate Interest are the key lawful reasons for processing data. In the case where CES Communications is the data controller (Contractors, Suppliers, Clients) Consent and Contract will be the over-riding principles for data processing with Legal Obligation available as required in the vetting of associates as may be required from time to time for adequate HR management.
Under the terms of our DPA, the data controller will be informed of their obligations to the data subjects and are responsible for ensuring that all communications as generated through CES Communications is approved from the content to the opt-out and including the request to access, and requests to be forgotten.
Regarding Consent
CES Communications relies on the data controller to establish consent from the users with which they wish to communicate with. In the absence of consent, it is assumed that that client is proceeding to use CES Communications under the lawful reason of legitimate interest.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Data Retention
CES Communications has strict policy on data retention with respect to the length of time they will keep PII provided from the data controller’s. The PII will be prescribed a time frame before automatically being deleted, usually 14 days, 90 days or automatic deletion at 120 days. The controller may wish to resend the data and under those circumstances, the prior history associated to the non PII fields will still remain in the system as this is a requirement to adequately ensure we are respecting the rights of the data subjects.
CES Communications will retain internal data for only as long is necessary to complete the requisite transactions that may be taking place with that subject. In the event that a lifetime contract has been agreed to CES Communications will retain anonymized data in order to continue performing the required contractual obligations.
Contact us today to find out more about how we receive, secure, store, process and dispose of data with the balance of client interest and end-user privacy in mind.
Contact Us
Contact us today for more information on what CES Communications can do for you.

